Cyber threats have become increasingly salient for most organizations, with potentially fatal
consequences in terms of operations, finance and reputation. The business must realize the
enormous growing of such threats – and the hard, cold fact that cyber-attacks are no longer a matter of “if”, but a matter of “when?”.
Every organization nowadays needs of an efficient shield against potential threats and as such a
transition towards an effective InfoSec Governance is the only way ahead. A clear, simple and consistent security mindset and practices must be embedded at every level of the organization. For many organizations, this is no longer a matter of awareness development, but a profound matter of cultural
change.

From an information security perspective, companies often have perceived their own organization as a castle with well-defined walls, with few entry points sufficiently staffed with guards monitoring what information is coming in or leaving the organization. If further protection is needed, it is obvious what to do: build higher or thicker walls or add additional security guards. What is inside the castle can be considered safe.
However, there have been several significant changes in the past few years as:
○ New business models and supply chain dependencies transcending traditional company and information boundaries
○ Advances in technology and digitization increase ICT reliance
○ Increasing reliance on external parties and their security approach
○ Scarcity of resources, be it financial or human resources
○ Increased regulatory requirements supporting the shift from a protection focus to a detection/response focus (e.g., GDPR)
○ Changes in the cyber threat landscape (e.g., crime-as-a-service, espionage)
This means that reliance on traditional security perimeter is no longer sufficient, a mindset that information security professionals have been advocating for several years and new ideas and approach have to be implemented.
A new vision of adoption could be for example the following points:
The next generation CISO
Why so many companies are still struggling to achieve this approach? A CISO of a reputable company once said: “I was hired for my technical security skills; however, I do not know how to build an organizational change program.” The next-generation CISO not only needs an understanding of security challenges, but also needs to deliver this change in a programmatic approach.
The need for a step-change in information security
What is needed is a way to package the NIST thinking into an information security transformation framework considering the organizational model of companies.
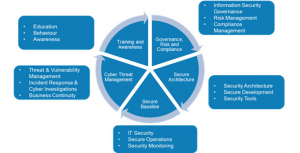
The goal of the different components:
– Governance, risk and compliance: Align the approach to the company’s governance model and build alliances with related functions, such as risk management, corporate security, compliance and audit.
– Secure architecture: Ensure a ‘security by design’ approach.
– Secure baseline: Do the fundamental things right (e.g., patching, monitoring, adopting good IT operations practice).
– Cyber threat management: Understand the threat environment and provide appropriate incident response.
– Training and awareness: Address the human factor in information security.
Define KPIs
One key element is the definition of KPIs to measure the progress for each framework component. These KPIs help to communicate the benefits of a multi-year program to senior management. The assignment of skilled project/program management resources also helps to maintain the focus rather than daily operational tasks superseding project/program goals.
Experience so far
In the last years in cyber security landscape we are experiencing many changes in this field as:
– Shift toward a holistic view: from a tool discussion to a capability-based discussion covering people, process and technology.
– Regular re-assessment of capability profile, threat landscape and business strategy define the security projects for the coming year.
– Capability needs drive security strategy and implementation priorities.
– A failure to meet incident resolution target KPIs resulted in a root cause analysis and renegotiation of service level agreements (SLAs) with vendors.
New threats demand a new mindset – and approach – for information security professionals.








